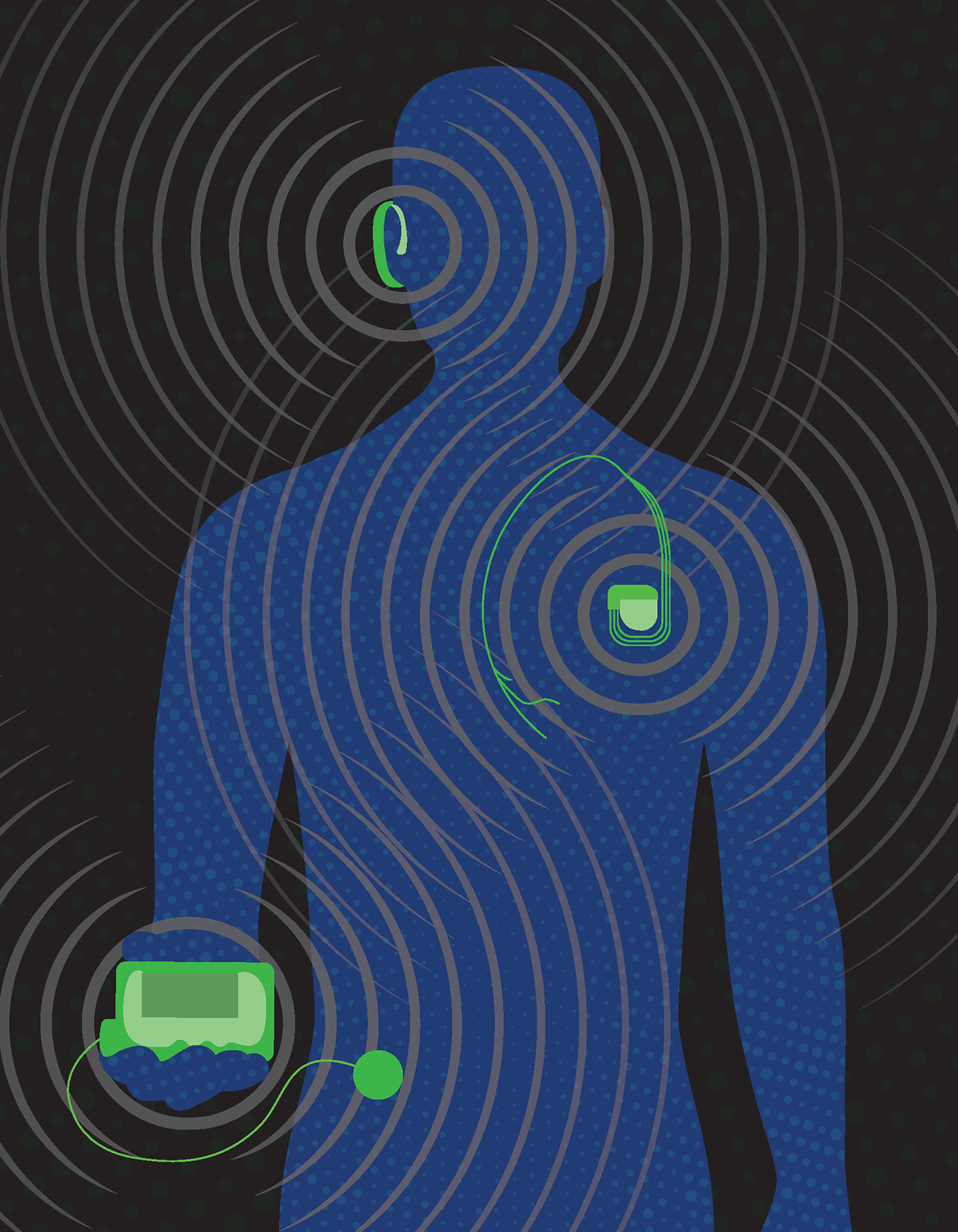
“Hacking of hearing aids can be spying-related. All of the audio data can be intercepted, so they can essentially just listen in on our conversation, and they can even grab geolocation data . . . so there’s a huge variety of exploits associated with IoT devices.” – David Baldwin
(Illustration: Susanna King, SRNL)
Wireless technology has become ubiquitous. In our kitchens, our workplaces and our pockets, we are increasingly surrounded by and dependent upon wireless communication. This electronic ecosystem has even been given a name – the Internet of Things (IoT). These devices have greatly enhanced our lives and increased our productivity, and in the process made the world dramatically more connected.
While this connectivity is generally a net positive, it has made us more vulnerable to nefarious motives. Not a week goes by that we don’t read about a cybersecurity breach, and unfortunately many of us have personally been the victim of such a crime. Having our information or money stolen as part of a computer hack is a constant concern these days, but electronic privacy and safety concerns have extended to the medical field. Wireless devices vital to our health and wellness have become commonplace in doctors’ offices, hospitals, the military and even on and in our bodies. As such, these devices are potentially vulnerable to cyber attack.
A group of researchers at Savannah River National Laboratory is attempting to change that. It is led by David Baldwin of SRNL’s Unconventional Cybersecurity Group and his project, Reverse Engineering of Medical Devices for Innovation and Advancement in Healthcare. The team is working in conjunction with joint appointee Jeffrey Morris and Michael Nowatkowski from nearby Augusta University.
Baldwin has had an interest in the medical IoT since his college days. “I had the opportunity to go to Black Hat, which is a very large cybersecurity conference hosted in Las Vegas,” said Baldwin. “My favorite talk while I was there was a group that talked about hacking insulin pumps, pacemakers and other medical technology. I saw the vulnerabilities these devices have, and that the device developers downplayed them.”
Baldwin determined that it was imperative and vital that research into medical device hacking be undertaken, and that it be conducted by third party scientists who did not have a financial interest in the devices’ success. When Baldwin came to SRNL he discovered a nascent effort in this space was underway at the lab, and he inherited the effort when the principal investigator moved on.
Baldwin explained that there are a multitude of cyber hazards associated with IoT medical devices. So-called “White Hat” hackers, those who discover vulnerabilities for patching before malicious actors can exploit them, determined that heart attacks can be induced in those with pacemakers. In addition, hackers can cause insulin pumps to discharge all of their insulin at once, with potentially fatal consequences.

David Baldwin examines the computer code from a medical device. (Photo: LJ Gay,
SRNL)
Medical device cyberattacks can be leveraged to collect data and information as well. “Hacking of hearing aids can be spying-related,” said Baldwin. “All of the audio data can be intercepted, so they can essentially just listen in on our conversation, and they can even grab geolocation data . . . so there’s a huge variety of exploits associated with IoT devices.”
Baldwin’s research is focused primarily on existing medical devices. Common weaknesses in these devices are in a broad spectrum that applies to similar devices in general, but each specific instrument has its own individual vulnerabilities. The goal is to analyze the vulnerabilities in a handful of devices to understand the methodology that can be utilized to leverage general weaknesses associated with IoT devices, which will also help with the design life cycle of new ones.
Medical devices are increasingly dependent on usage with handheld devices such as cell phones or tablets. This allows the medical device to be simpler, easier to use and cheaper to design and manufacture. The interaction a cell phone has with the medical device via Bluetooth and Wi-Fi represents the most common vulnerability, explained Baldwin.
The group has been working with Augusta University on the electronic security of IoT portable ultrasound devices. These devices can be dependent on Wi-Fi networks that can be pinpointed when turned on, potentially giving away their location. The group is also analyzing a Bluetooth hearing aid that is available without a prescription. This scenario could lead to supply chain vulnerabilities, as well as security issues with the signal encryption and both the hardware and software.

A CT scan of a medical device. (Photo: Vincent Dinova)
Baldwin indicated that Bluetooth devices can be susceptible to a “man in the middle” attack, whereby the hardware address of the device and cell phone are stolen. Then the hacker can break the connection between device and cell phone, essentially posing as one or the other. They can intercept all of the data coming from one of the devices, with both devices unaware of the breach. The process of reverse engineering the device for the purposes of determining electronic vulnerabilities starts relatively low-tech. “Typically when you get a new device you look at the user manual and any other technical documents for the device,” said Baldwin. “To comply with the FCC, they have to tell you all of the different ways the device communicates . . . and the encryption levels.”
The next step is to determine if similar devices have had vulnerabilities. Databases can provide information about these, known as common vulnerability exposures (CVE) and common weakness exposures (CWE). Existing methods of attack can then be tested on the device. The software can be broken down into C and assembly code, which can be analyzed for potential electronic security issues. Moreover, the team has CT scanning capability with the SRNL CT laboratory, which helps determine hardware security issues.
Solutions to cybersecurity issues with medical devices can vary. For example, something as straightforward as multi-factor authentication can be used. The device hardware can be designed to be more resilient against certain exploits, and the direct communication signal via the cell phone can be hidden. However, proper encryption specific to the device is usually the best option.
The size of the medical device market and its electronic security present challenges and opportunities for research in the field. “It is a massive market projected to soon be close to a trillion-dollar market cap,” indicated Baldwin. “Thus, our work is primarily for proof of concept. That’s how we are going to have the biggest impact on this ecosystem.”

A device is tested in an environment with no external communication interference. (Photo: Mitchell Jordan)